Challenge 2 - Garbage
Description
One of our team members developed a Flare-On challenge but accidentally deleted it. We recovered it using extreme digital forensic techniques but it seems to be corrupted. We would fix it but we are too busy solving today’s most important information security threats affecting our global economy. You should be able to get it working again, reverse engineer it, and acquire the flag.
Download - garbage.7z
Contents
Solution
Intro
tl;dr: Fix truncated binary with padding, unpack with UPX and fix import table, remove application manifest, run binary.
In this challenge we were given a single file, garbage.exe.
Initial Analysis
garbage.exe is a PE file that has been packed with UPX.
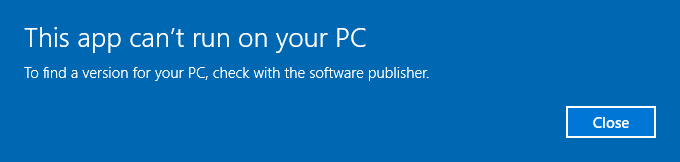
Attempting to run the file results in an error. Though this is expected, as the challenge description mentions the file being corrupted. Also, since the file is corrupted, it can’t be unpacked just yet, we will need to fix it first.
Finding and Fixing Truncation
Let’s open up the file in a hex editor and take a look.
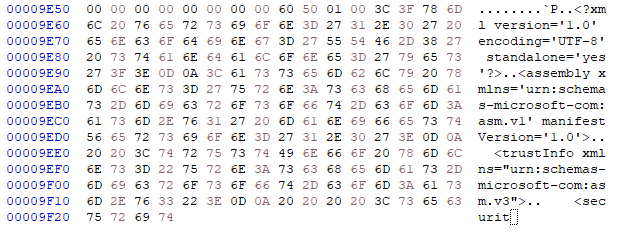
Scrolling to the bottom we can see that part of the application manifest has been cut off.
An application manifest is an XML file that describes and identifies the shared and private side-by-side assemblies that an application should bind to at run time. These should be the same assembly versions that were used to test the application. Application manifests may also describe metadata for files that are private to the application.
I copy-pasted an example manifest I found over the corrupted one and saved the file as garbage_fixed_manifest.exe, but unfortunately the program still doesn’t run or unpack.
Opening garbage_fixed_manifest.exe in PE-Bear and viewing the Section Headers reveals the issue.
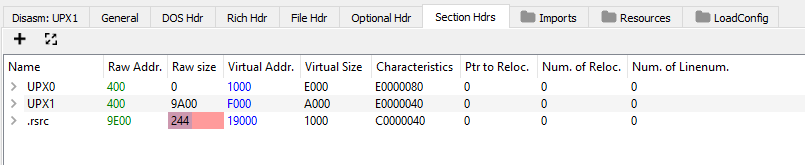
Notice how the Raw Size for the .rsrc section is colored red? This indicates the Raw Size is wrong, double clicking the cell shows the expected value of 400.
To fix the corrupted file, I padded the end of the file with 0x400-0x244 (0x1BC) null bytes.
Now the binary runs, but we get a different error…
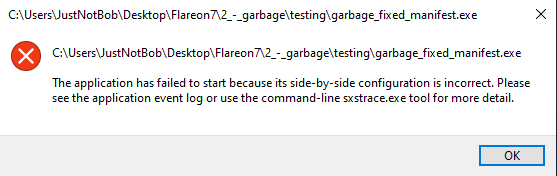
Unpacking and Fixing Imports
The next thing I try is unpacking the binary with UPX and once again opening it in PE-Bear.
I unpack the binary with the following command: upx.exe -d .\garbage_fixed_manifest.exe
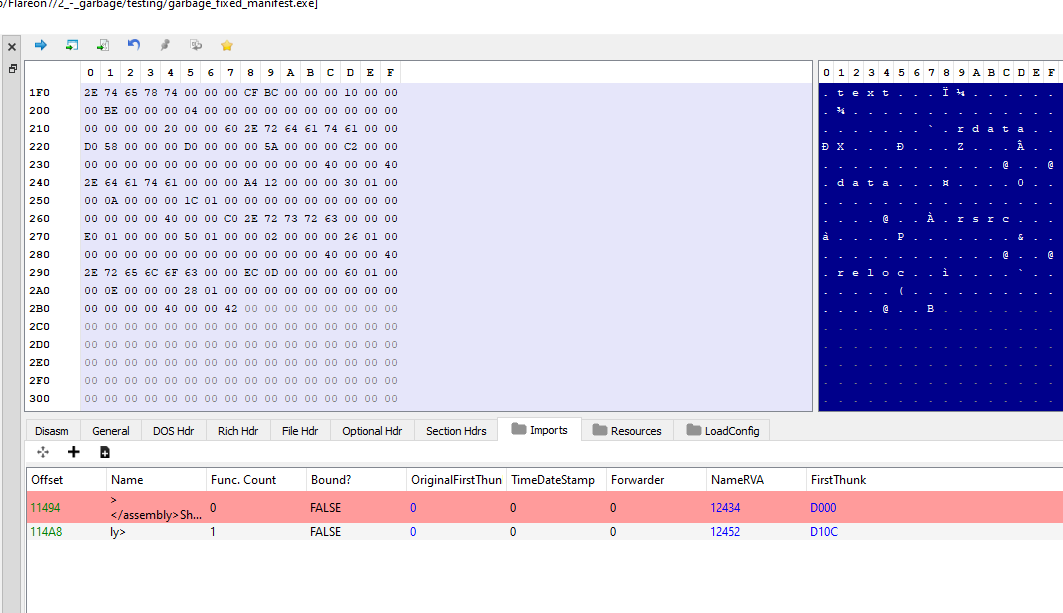
Now I see that the import table is also broken, clicking on NameRVA will give hints to the name of the imports we need…
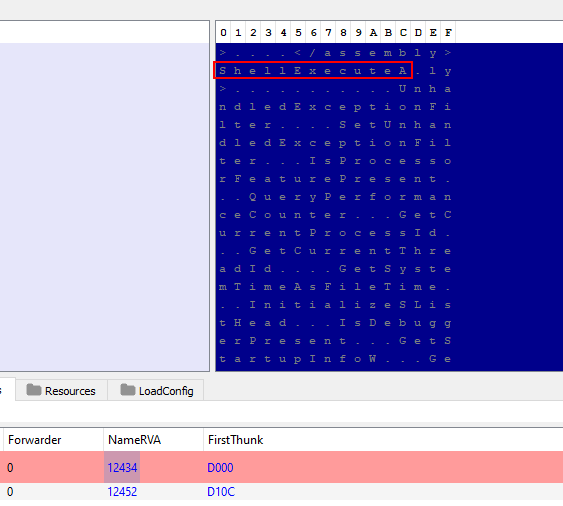
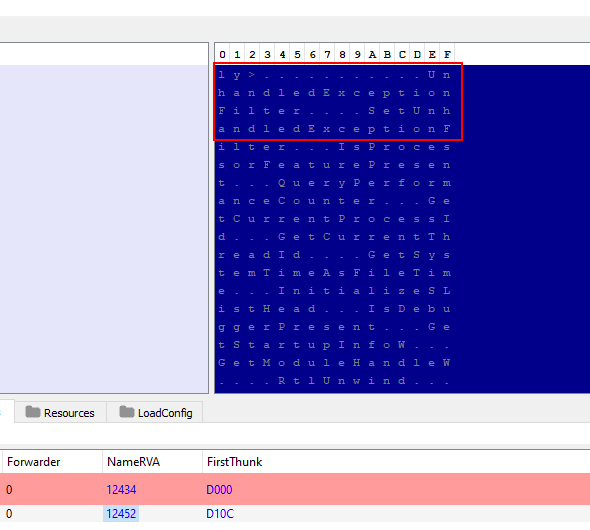
Looking up ShellExecuteA and UnhandledExceptionFilter we find that they are part of Shell32.dll and Kernel32.dll respectively.
So I rename the missing imports and save the file as garbage_fixed_imports.exe
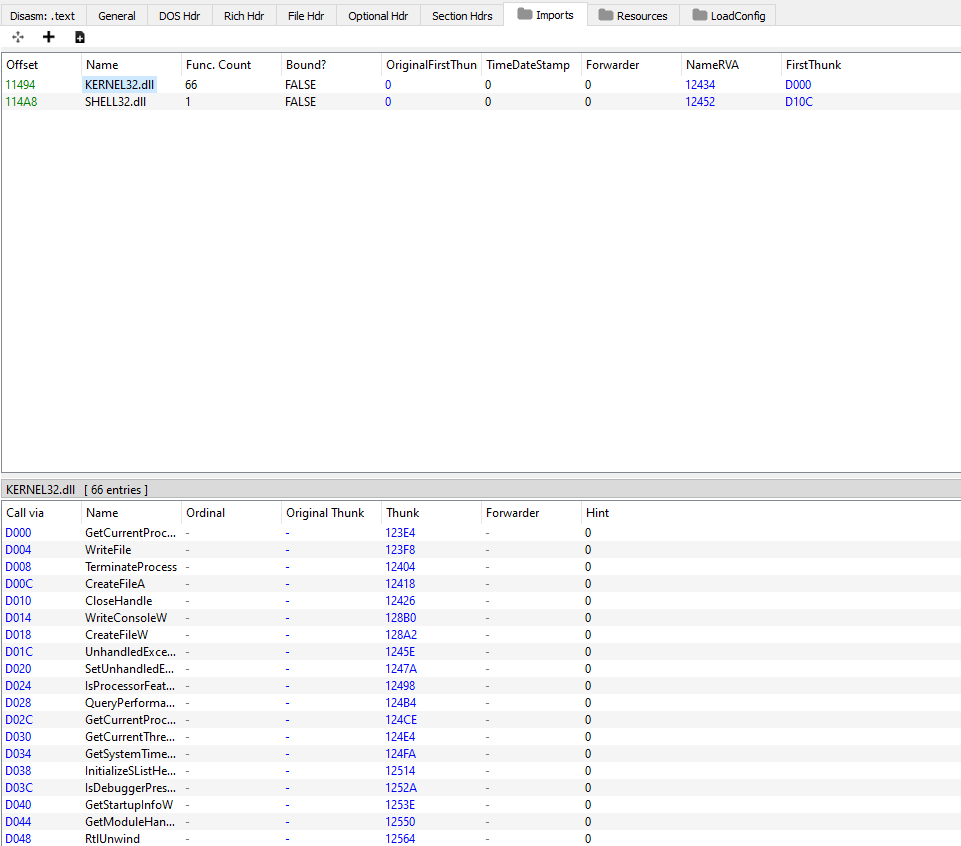
However, trying to run the binary still results in the “side-by-side” error.
Another Broken Manifest
I open the binary in CFF Explorer and notice the application manifest is cut off again.
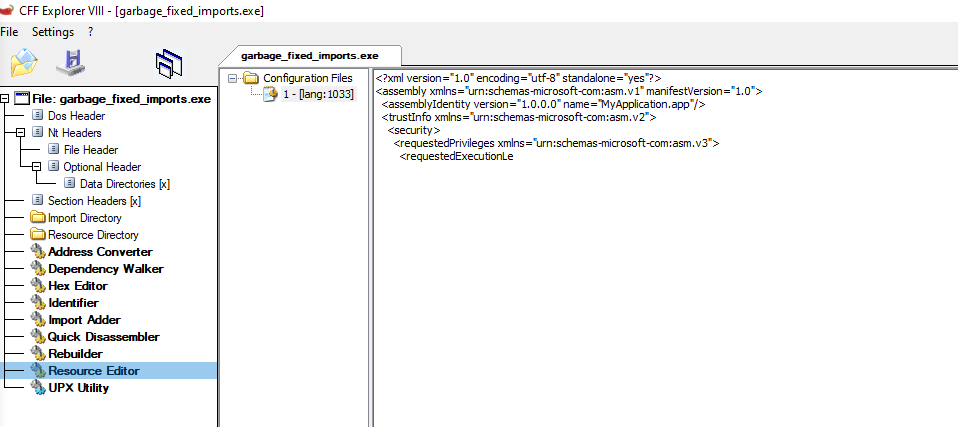
This time, I delete it completely and save the binary as garbage_fixed_imports_and_manifest.exe.
Flag
The binary finally runs sucessfully and we are presented with the flag.
The binary actually writes a vbs script (sink_the_tanker.vbs) to the current directory and runs it. The vbs script just contains the code to display the pop-up with the winning text.
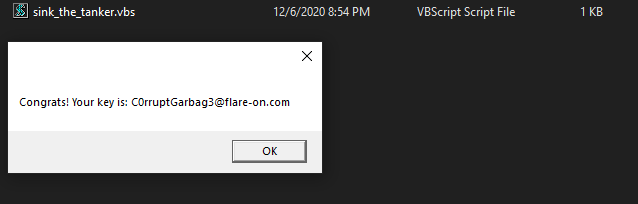
Flag: C0rruptGarbag3@flare-on.com