Challenge 4 - darn_mice
Description
“If it crashes its user error.” -Flare Team
Download (password: flare) - 04_darn_mice.7z
Contents
Solution
Intro
For this challenge, we’re given a single executable, darn_mice.exe.
Let’s start off by trying to run the program.
Initial Analysis
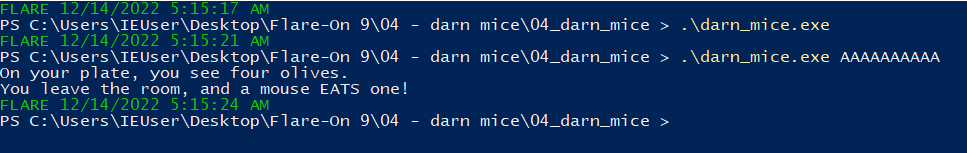
Double clicking the executable just brings up a window and immediately closes. Executing the program with arguments brings up an interesting message.
Time to open up Ghidra and see what’s going on. Let’s start off by searching for the strings we observed earlier:
- “On your plate, you see four olives.”
- “You leave the room, and a mouse EATS one!”
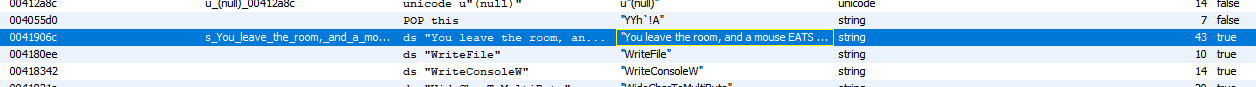
One apperas to be at 0041906c.
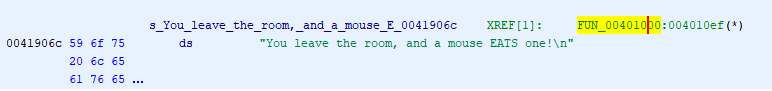
Double clicking that string and following the xref brings us to FUN_00401000.
Exploring FUN_00401000
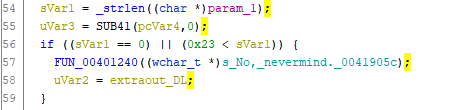
At the beginning of the function, there are some values being assigned to array local_2c.
Further down on lines 53 and 61, we see the strings that were initially printed out after executing the program.
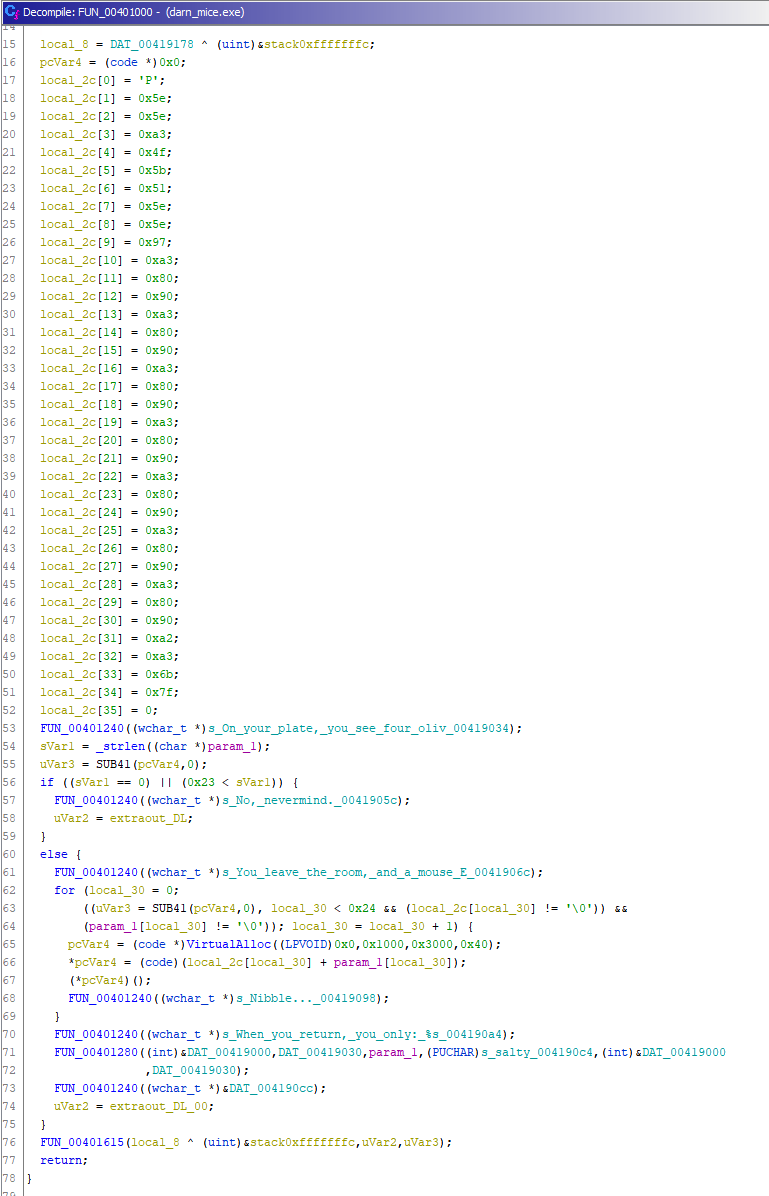
The code below gets the length of param_1 and checks if it equals 0 or is greater than 0x23 (35 in decimal).
I have a hunch that param_1 is the argument we pass to the program, let’s test that theory.
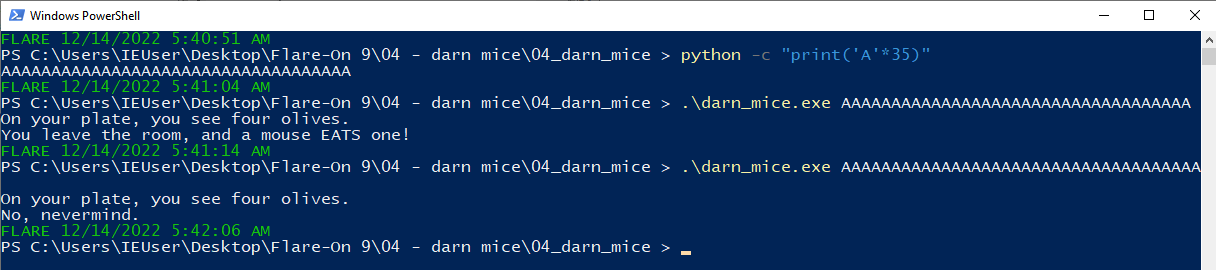
Seems like our assumption was correct, so we know our argument can’t be more than 35 characters long.
Continuing on, the code loops through our input and the local_2c buffer, adds the values together, and then tries to execute them (*pcVarf4();) So to avoid any crashes, we need to have the values add up to valid x86 assembly.
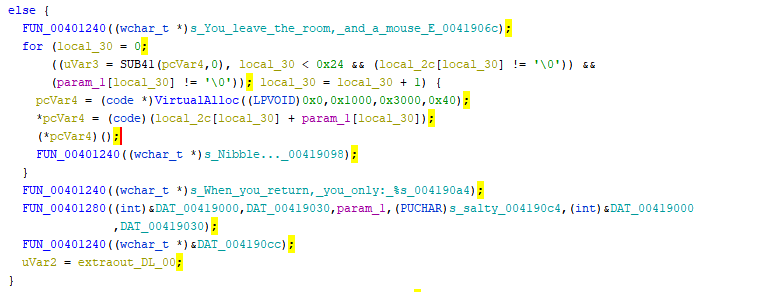
My first thought is to just have the code return. In order to do that, each character in our input and the values in the local_2c buffer need to add up to 0xC3, which decodes to the RET instruction. We can throw together a quick python script to calculate this.
Python Solver
I copy the hardcoded values from Ghidra into my Python script and it printed out a nice looking string.
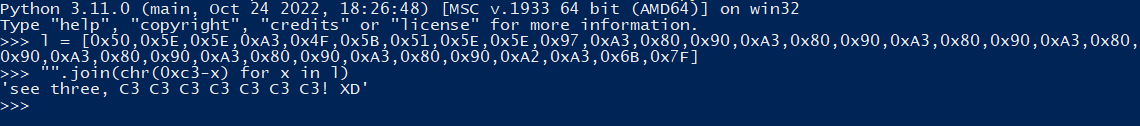
Using that string as our input gives us the flag.
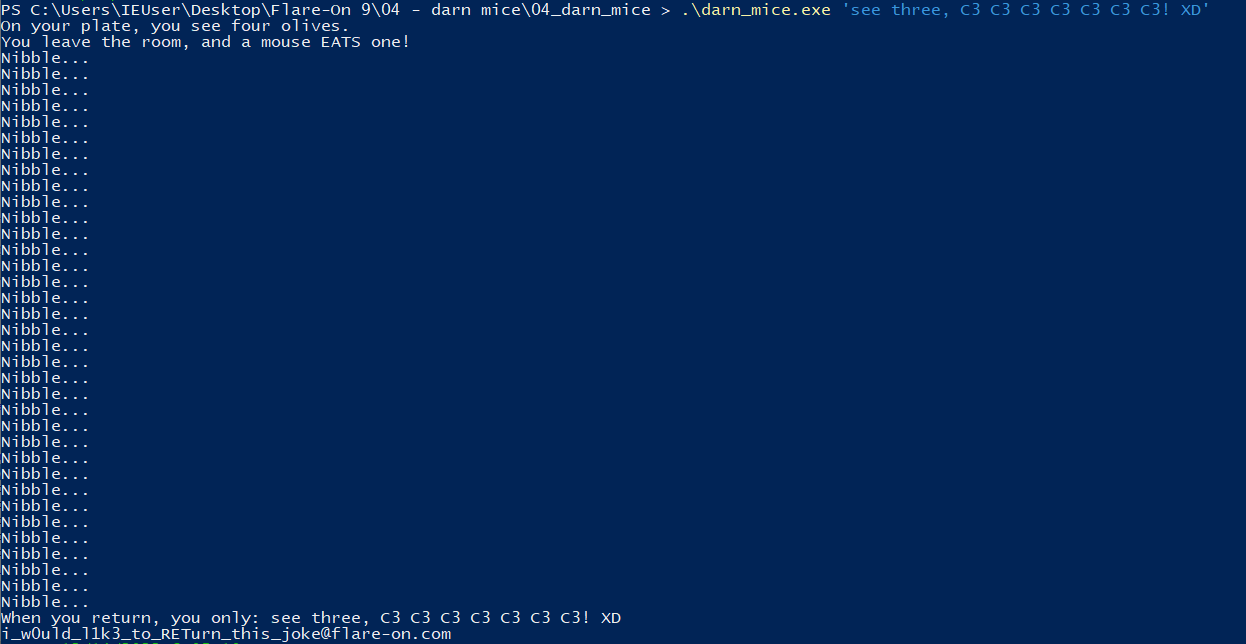
Flag
Flag: i_w0uld_l1k3_to_RETurn_this_joke@flare-on.com