Challenge 3 - Magic 8 Ball
Description
You got a question? Ask the 8 ball!
Download (password: flare) - 03_magic8ball.7z
Contents
Solution
Intro
For this challenge, we’re given a handful of files and assets.
While it’s totally possible we’d have to reverse the dlls, I’m guessing that we only need to focus on the exe and the rest are just necessary to run the challenge.
Initial Analysis
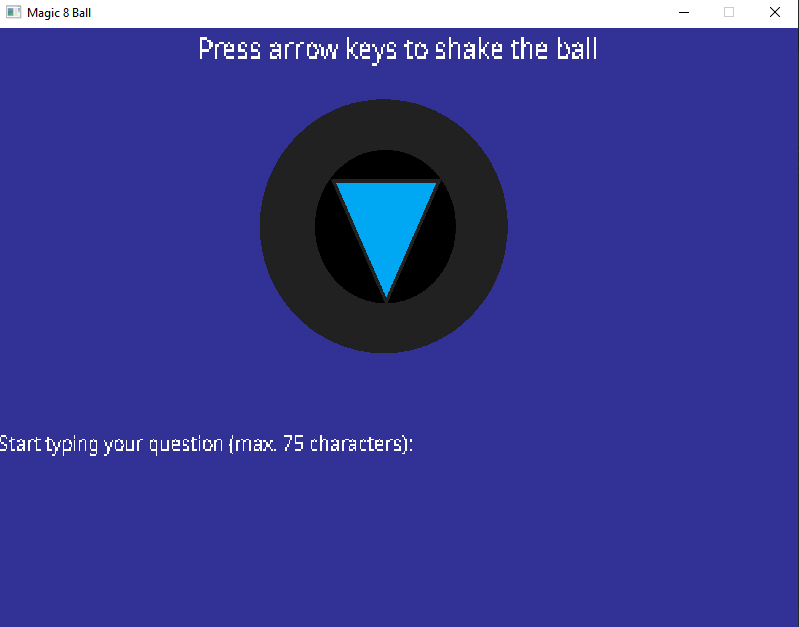
Running the program brings up an 8-ball. We can type in text and use the arrow keys to shake the ball.
Typing some text and hitting enter shows a randomly generated message on the 8-ball.
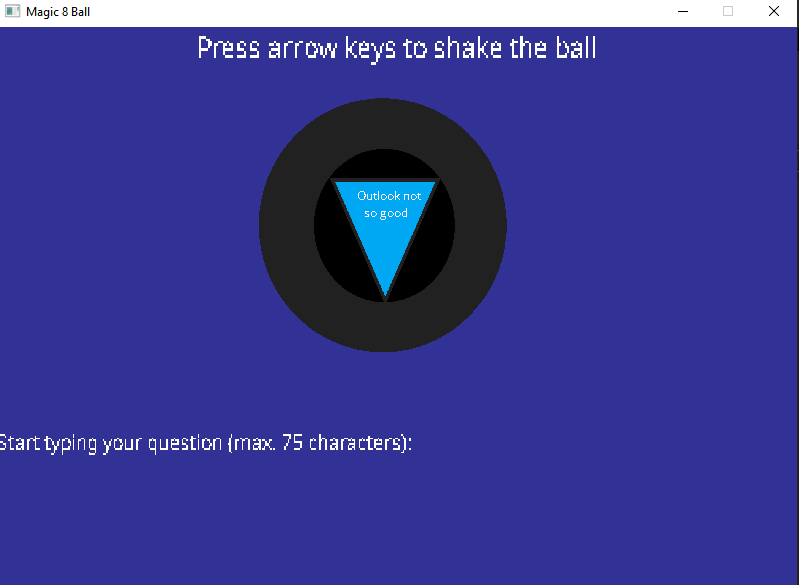
I take a guess that we need to enter some type of password to get the flag. (This ends up being half correct.) Let’s dive into Ghidra to see what we can find.
Magic Sequence
Clicking through the different functions, I come across the following sequence of comparisons in function FUN_004024e0 that ends with a strncmp.
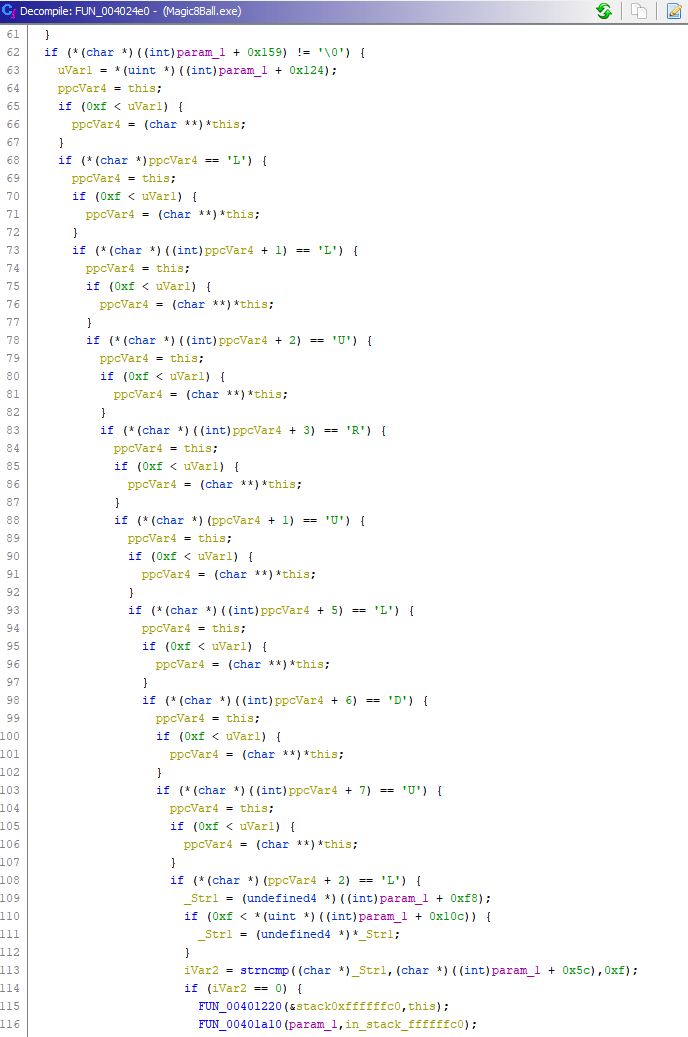
I make another educated guess that the various letters (L, R, U, D), map to each respective arrow key, (Left, Right, Up, Down). So judging from the sequence, it looks like we have to hit the arrow keys in the following order: Left, Left, Up, Right, Up, Left, Down, Up, Left. Then the program checks our inputted text against some value and I assume it would give us the flag. Let’s try it out in a debugger.
Debugging
I open up the program in x32dbg and search for the strncmp call in the current module.
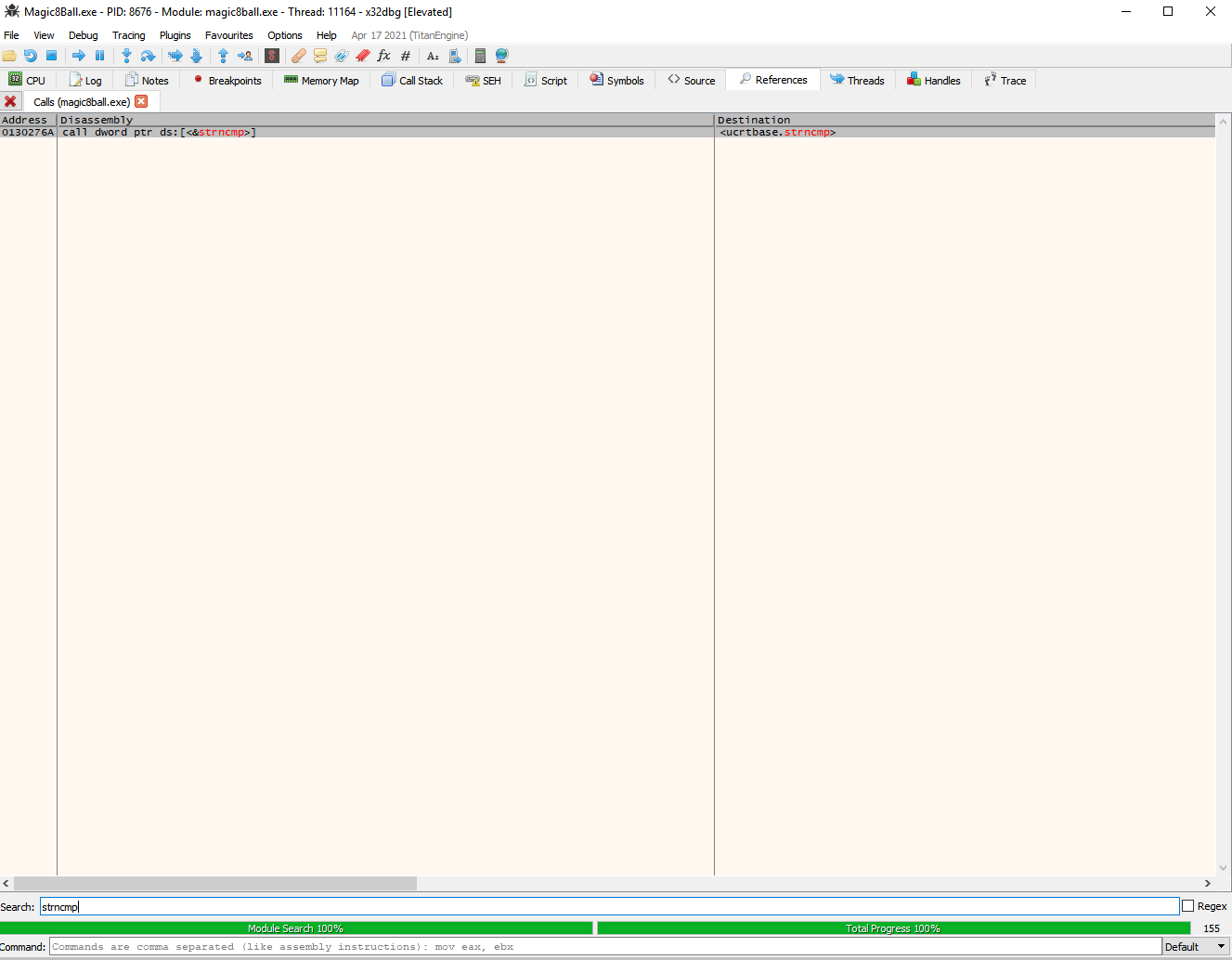
Next, we double click the call from the search results and set a breakpoint on it. We run the program from the debugger and ensure that the program is fully loaded and the game window pops up.
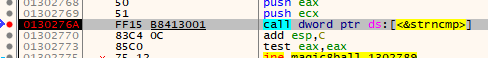
Entering some dummy text and hitting the magic arrow sequence followed by the Return key triggers the breakpoint.
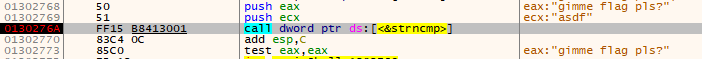
Now we can see the arguments to strncmp in the screenshot below being pushed to the stack.
- EAX =
gimme flag pls?
- ECX =
asdf
Flag
Restarting the debugger and entering the password: gimme flag pls? along with the magic arrow sequence gives us the flag.
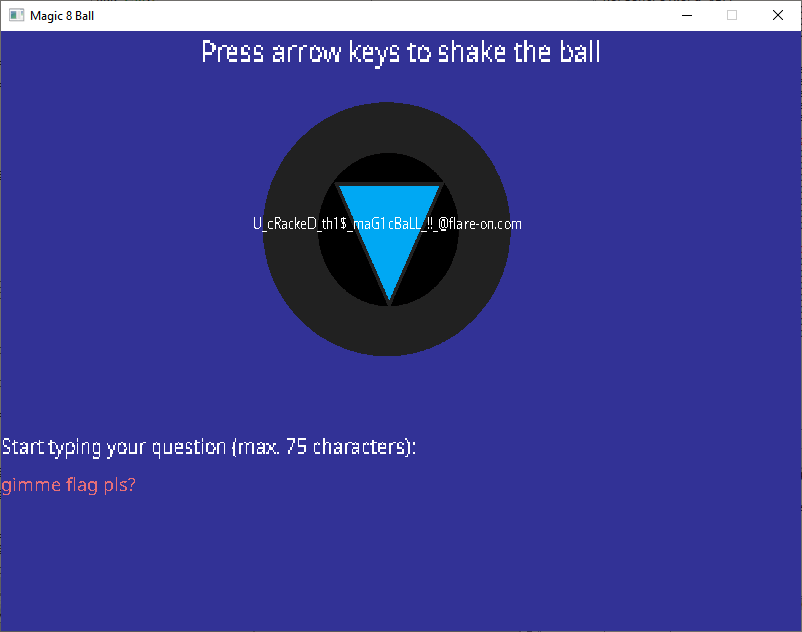
Flag: U_cRackeD_th1$_maG1cBaLL_!!_@flare-on.com